Client Project: Accounting Firm New Client Onboarding Form with Jotform
Client onboarding taking longer than it should?
See how Jotform, when set up properly, can simplify forms, reduce admin, and improve client experience for Australian businesses.
.png)
What Are DKIM and DMARC – and Why They Matter for Business Email Security
Most email scams don’t start with a virus or a hacked system - they start with an email that looks legitimate. DKIM and DMARC are two simple but powerful controls that help protect your business from impersonation, phishing and email fraud. Here’s what they are, how they work, and why they matter.

Need complex forms for your website? Jotform might be the answer
Learn how Jotform helps small businesses replace emails, PDFs, and spreadsheets with smarter, automated forms.

Tech Tips: Microsoft Word from document recovery to Quick Parts
Gone are the days of Microsoft Office suites beloved assistant Clippy popping up to offer you some help to compose documents, but never fear, we may not be a slightly unsettling paper clip with eyes but we have put together a selection of tips to help make your Microsoft Word experience a little bit better

Notion Explained: An Organisational App for Small Businesses
| Notion is a popular all-in-one organisational app that helps small businesses manage tasks, documents, and projects. We have created a blog providing an overview of its key features and how they can support Australian businesses. |

Tech Tips: Microsoft Teams Tips to Save Clicks, Time, and Sanity
Microsoft Teams is packed with little features that can make a big difference once you know where to find them - but let’s face it, we’re all busy people. So we’ve put together this blog to help you get the most out of Teams, faster.

Client Project: Penetration Testing to comply with the Safer Technologies 4 Schools Framework
Recently, our team at FortiTech was engaged to undertake penetration testing for a client as part of their efforts to align with the Safer Technologies 4 Schools Framework.
Our top blog posts of 2025
| Wondering what everyone was reading in 2025? From smarter Google searches to better cybersecurity and business planning, these five blogs stood out as the most popular with our readers over the past year. |

Cybersecurity Awareness Training for a Financial Services firm
Each November we conduct Cybersecurity Awareness Training to help one of our Financial Services clients meet the requirements of their cyber liability insurance, and this year was no different. Connecting in via Zoom to their boardroom David walked the team of 14 through the latest in cyber threats and practical steps on avoiding being scammed.

Client Project: IMAP to Microsoft 365 migration
Still using IMAP for email? It might be holding your business back - and here’s why one Gold Coast engineering firm decided to make the switch. Find out how in our latest blog.

Tech Tips: How to create a QR code
Want to streamline your customer experience? QR codes are a simple, cost-effective solution for Australian small businesses. Read our latest blog to find out how to create one and use it safely.

The Ultimate Server Buying Guide for Australian Businesses
Learn how to choose the right server for your business. From specs to backups, this guide makes server buying simple and secure.

Benefits of an Uninterruptible Power Supply (UPS) for Your Business in 2025
Discover why Brisbane businesses need UPS systems more than ever in 2025. Learn about benefits, costs, and applications to protect against outages during a stormy summer.
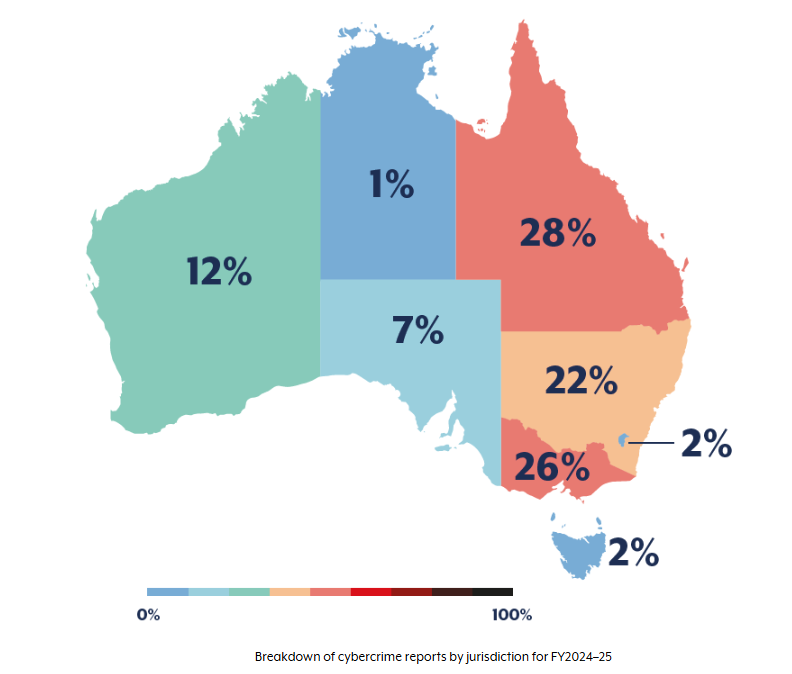
Cyber Threats on the Rise: What Australian Businesses Need to Know from the ACSC 2024–25 Report
The ACSC’s latest Cyber Threat Report reveals a 50% spike in the average cost of cybercrime, with attacks growing in scale and sophistication. From business email compromise to state-sponsored threats, no organisation is immune.

Tech Tips: Top 5 Tips to Secure Your Business Social Media Accounts
Discover 5 essential tips to secure your business social media accounts. Protect your brand from scams, hacks, and phishing attacks today.
.png)
Client Project: Penetration Testing for Insurance Compliance
Discover how a recent penetration test uncovered hidden vulnerabilities for an Australian financial services provider—and why regular security assessments are now essential for insurance, compliance, and peace of mind. Learn what’s involved, what’s at stake, and how expert testing can safeguard your reputation and bottom line.

Client Install: Extending Wi-Fi Coverage to a Shed Office
Need better Wi-Fi coverage? See how FortiTech used TP-Link Omada to extend business-grade Wi-Fi to a shed office with gigabit speeds.
