Australian businesses face increasing pressure from insurers, regulators, and customers to demonstrate robust cybersecurity practices. One of the most effective ways to meet these expectations—and to protect your business from costly breaches—is through regular penetration testing and vulnerability assessments.
Recently, our team at FortiTech was engaged by a mid-sized Australian financial services provider (let’s call them “Acme Insurance Group”) to conduct a comprehensive penetration test of their public-facing web services used by their brokers. This engagement highlights not only the importance of penetration testing for compliance and insurance purposes, but also the value of working with experienced professionals who understand the unique needs of Australian businesses.
What is Penetration Testing and Why Does it Matter?
.png)
Penetration testing, often called “pen testing,” is a simulated cyberattack against your IT systems to uncover vulnerabilities before malicious actors can exploit them. For many Australian businesses, penetration testing is no longer optional—it’s a requirement for cyber insurance policies, regulatory compliance (such as PCI DSS for payment processing), and industry best practice.
A well-executed penetration test provides actionable insights to reduce your attack surface, strengthen your defences, and validate the effectiveness of your existing security controls. It’s not just about ticking a box for compliance; it’s about protecting your reputation, your customers, and your bottom line.
Our Approach: Industry Standards and Real-World Threat Simulation
For Acme Insurance Group, we followed a rigorous methodology aligned with the OWASP Testing Guide, NIST 800-115, and PCI DSS standards. These frameworks are recognised globally and ensure that our testing is thorough, reliable, and relevant to the threats Australian businesses face.
Our process combined leading cyber security assessment tools—such as Nmap, Nikto, SSLyze, OpenVAS, and targeted manual checks—to simulate the tactics of real-world attackers. Importantly, we performed the test in a “black box” manner, meaning we had no prior knowledge of the client’s systems beyond their public IP address and domain. This approach mirrors the perspective of an external threat actor and provides the most realistic assessment of your exposure.
Scope of the Engagement
The scope included:
- The primary business domain and its associated public IP address
- All public-facing web applications and network services
- Web server security configurations (HTTPS, HTTP headers, SSL/TLS settings, cipher suite strength)
- Vulnerability scanning against the latest CVE database
Key Findings and Recommendations
Our assessment uncovered several important findings, ranging from high-risk vulnerabilities to best-practice recommendations:
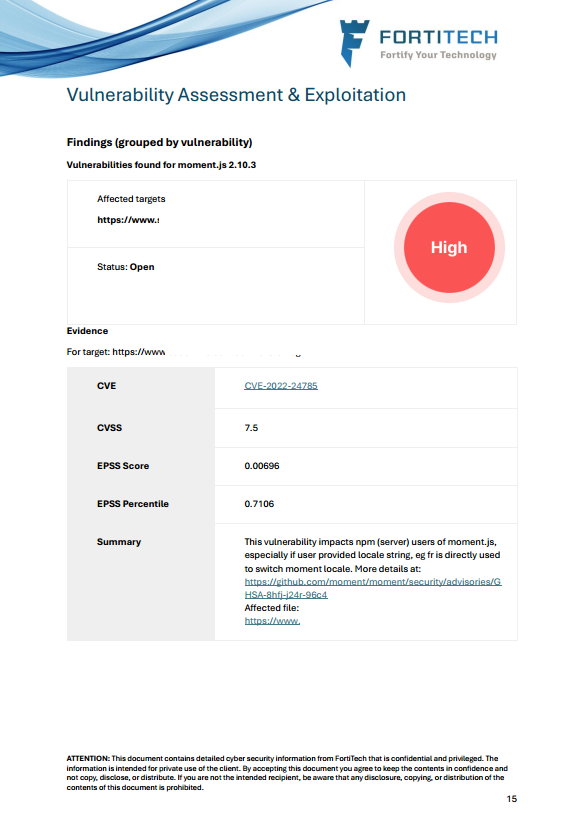
1. Outdated Software Components
We identified a high-risk vulnerability in an outdated JavaScript library (moment.js), which had several known CVEs. Outdated software is a prime target for attackers, as exploits are often well-documented and actively used in the wild.
Similarly, a medium-risk vulnerability was found in an older version of the Bootstrap framework. While not immediately critical, these types of issues can be leveraged in multi-stage attacks and should be addressed as part of ongoing maintenance.
2. Missing Security Headers
Several low-risk but important security headers were missing, including Referrer-Policy, Content-Security-Policy, and X-Content-Type-Options. These headers help prevent user tracking, cross-site scripting, and MIME-type attacks. Implementing them is a straightforward way to harden your web applications against common threats.
3. SSL/TLS Configuration
The client’s web server was using a wildcard SSL certificate with a 2048-bit key, valid for several years. While this meets current standards, we recommended moving to a 4096-bit key and a 12-month certificate validity period, in line with NIST recommendations. We also advised enabling only TLS 1.3 for improved security and performance.
4. Information Disclosure and Login Security
We found that server software and technology details were exposed in HTTP headers and meta information, which can aid attackers in crafting targeted exploits. We recommended minimising this exposure wherever possible.
Additionally, the login interface was identified as a potential target for brute-force attacks.
Why Choose FortiTech for Your Penetration Testing Needs?
We don’t just run automated scans—we combine advanced tools with manual analysis to uncover issues that others might miss.
Our reports are clear, actionable, and tailored to your needs, helping you demonstrate due diligence to stakeholders and regulators.
As part of our commitment to thorough and actionable security, we offer a complimentary retest within 14 days of your initial penetration test. This allows your team to address any vulnerabilities identified, and then have us verify that the fixes are effective—all included in your original fee. Retests outside this window can be arranged for an additional cost, ensuring flexibility for your business needs.